
SOC 2 Type I Attestation
Richweb Receives SOC 2 Type I Attestation Independent Audit Verifies Richweb’s Internal Controls and Processes Glen Allen, VA – May

Enchantress of Numbers
Ada Lovelace, born as Augusta Ada Byron, was the only legitimate child of the famous poet Lord George Gordon Byron.

Spear Phishing is not a game
What is phishing? Phishing is one of the easiest forms of cyber attack for a criminal to carry out, but

Cultivating Excellence in Local School System
President of Pixel Factory Data Center Scott Brown knows the special skills Henrico CTE students can bring to the table. He - along

All About The Failover
"Apparently, according to our network services guy, where the outage was happening on the circuit and the fact that it
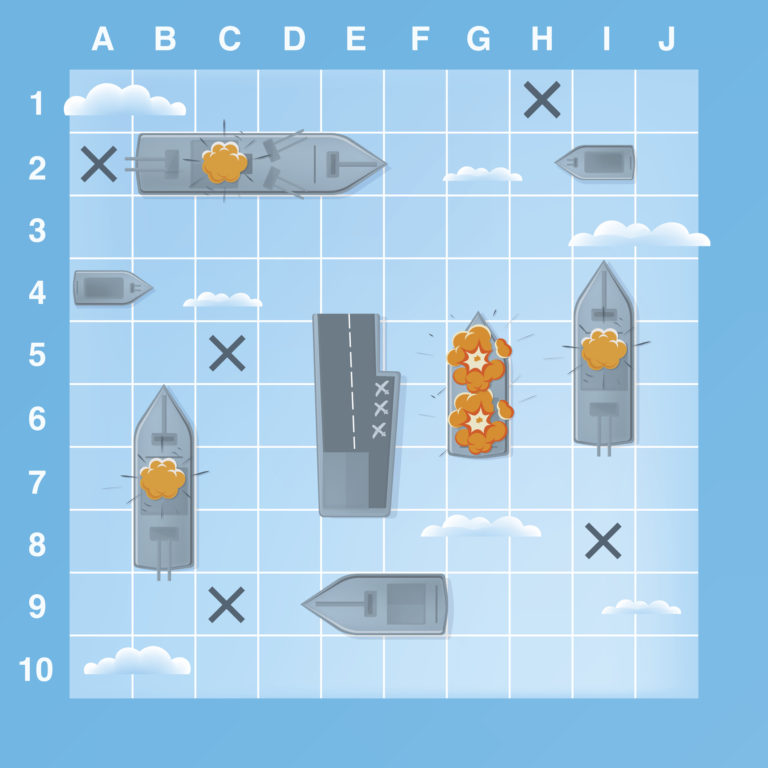
Playing battleships over BGP
Author of this blog post is BenJOJO: https://blog.benjojo.co.uk/post/bgp-battleships BGP is the glue of the internet. For a protocol that was produced

The importance to be a “busybox”
Busybox is a swiss army knife utility that is very useful for system recovery. Recently I had a server with

Bridging vs Routing Firewalls
A bridging firewall (sometimes called a transparent firewall) is a security appliance that does NOT actively participate in the routing

Clouds are not a cure-all
Make sure that you understand what you are paying for in the cloud. The ability to scale on demand is

Cron and Daemons: K2Awards Case Study
Purpose Demonstrate creative use of daemons and cron using K2Awards Background K2Awards has a complex trophy builder, called jthumb, that

You Are What You Eat
You are what you eat , they say. They say a lot of things and it is up to you
3 Creative, Unique Use Cases of PRTG
Not winning a contest sucks. This whole "it's not about winning" thing is a lot of nonsense. However, if participants
